Redvers COBOL Signature
The Redvers COBOL Signature software package combines asymmetric encryption (PKI) with digital signature technology in the form of RSA Laboratories PKCS #1, Digital Signature Standard (DSA) and Elliptic Curve Digital Signature Algorithm (ECDSA) standards.
Main features:
- All code is 100% pure COBOL
- Runs on any COBOL platform
- Supports public/private keys up to 4096 bits, passed in hex or Base64
- Supports RSA, DSA and ECDSA (elliptic curve) signatures
- Includes SHA-1 and SHA-2 224, 256, 384 and 512 bit hashing
- Distributed in COBOL source code
- Efficient, professional and fully scalable
- Supports calls from batch or on-line (eg: CICS)
- Free 30 day trial
The required security level for PKI cryptography and digital signature generation/verification, depends on the length of public/private keys as well as the choice of SHA-1 or SHA-2 hashing algorithms. Key sizes and hash digest lengths are specified by the calling application to ensure the correct security level is maintained.
Digital signatures provide assurance of the sender's identity and confirmation that the data received has not been altered by unauthorized activity.
How it Works
The diagram below shows how confidential information may be encrypted, signed, sent, verified and decrypted using the Redvers COBOL Signature software.
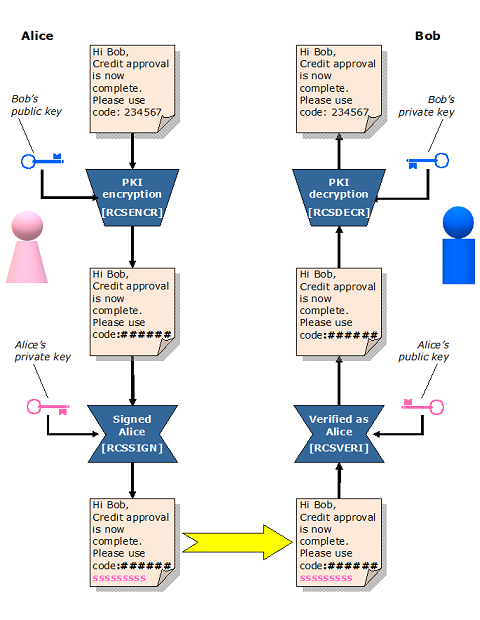
The Redvers Signature Software runs standard asymmetric encryption and digital signature algorithms, so that ciphertext and signatures can be decrypted and verified by external institutions running on any computer platform.
Technical Information
PKI encryption and associated OAEP padding logic complies with algorithms provided in the RSA Laboratories PKCS #1 v2.2: RSA Cryptography Standard. Specifically, RSAEP/RSADP are used for encryption/decryption and RSA-OAEP with MGF1 is used in padding and mask generation.
RSA signatures are also created and verified as specified in RSA's PKCS #1 v2.2: RSA Cryptography Standard. Signature logic currently uses the RSAES-PKCS1-v1_5 signature scheme, although RSASSA-PSS can be added on request. These signatures are particularly suited to JSON Web Token (JWT) transactions.
DSA signatures are created and verified as specified in NIST's FIPS PUB 186-4 Digital Signature Standard. All L/N bit lengths are supported: 1024/160, 2048/224, 2048/256 and 3072/256. DSA is similar to the EIGamal signature scheme.
ECDSA signatures conform to the ANSI ANS X9.62-2005 Public Key Cryptography for the Financial Services Industry - The Elliptic Curve Digital Signature Algorithm (ECDSA). All prime field curves are supported. Binary field curves can be added on request.
Redvers COBOL Signature 2.3 programs can be run on EBCDIC or ASCII character encoded platforms, using big or little endian binary formats. Data exchange between subroutines uses a common communication block containing left justified, space filled parameters in hexadecimal or Base64 formats. All subroutine storage areas containing confidential information are initialized before control is returned to the calling application.
The Software Package
The Redvers COBOL Signature software package consists of:
- A sample COBOL calling application program (RCSSAMP).
- Four additional application programs to encrypt (RCSENCR), decrypt (RCSDECR), sign (RCSSIGN) and verify (RCSVERI).
- Two Redvers Consulting subroutines (RCSCALC and RCSHASH).
All these programs should be copied to the standard source code library and compiled. RCSSAMP will need to be compiled and linked last, before starting the trial.
Included within the software is the Redvers calculator subroutine RCSCALC. This routine performs the modulated exponential calculations, modular inverse functions, scalar arithmetic and data conversion within the encryption/signature processes. Also included is the Redvers hashing subroutine RCSHASH, which runs SHA-1, SHA-224, SHA-256, SHA-384 and SHA-512 algorithms. RCSCALC and RCSHASH may be used by clients for other technical application requirements without charge.
If key lengths or algorithms are required that are not currently listed in the calling parameters, please contact your account manager or use our Contact page to request an enhancement.
